
Correction: Josh from Butterfly Labs has emailed me, there was no intrusion of any sort. They were testing some of their systems and adding new features.
While it did appear to be nefarious it seems that I jumped the gun, for that I apologize Josh assures me "everything is and has been secure."
The original post read;-
While pointing my browser at http://forums.butterflylabs.com/ I started to notice some strange things going on, namely that there were PHP errors being output at the top of the forum. While that in itself is not that unusual (I see it quite often when their database server gets overloaded due to the near constant DDOS that they receive) these were not your standard MySQL errors they are eval() errors.
[caption id="attachment_2208" align="alignright"
width="1291"]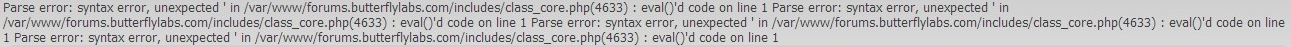 Click to enlarge.[/caption]
Click to enlarge.[/caption]
For those of you who are not PHP programmers eval is used in php to execute arbitrary code on the server and improperly handled it is one of the largest security holes in PHP. Even the PHP manual warns about its use in no uncertain terms warning;-
Caution
The eval() language construct is very dangerous because it allows execution of arbitrary PHP code. Its use thus is discouraged. If you have carefully verified that there is no other option than to use this construct, pay special attention not to pass any user provided data into it without properly validating it beforehand. The PHP manual
My suspicions were mounting , but what I saw next confirmed it for me, a post from Butterfly Labs forum moderator BFL_Josh posted up a 20 MB password dictionary to the site, commonly used in brute force attacks.
#
# This is a list of 2,151,220 unique ASCII passwords in sorted order according
# to their native byte values using UNIX sort command.
# This list (also known as wordlist, password dictionary or password list)
# is useful for password recovery tools such as John the Ripper, Hashcat,
# Aircrack-ng and KisMAC. To use this file, be sure to first remove these
# comment lines, i.e. the lines starting with # character.
#
# If you are looking for a better password dictionary,
# see http://[removed].com/u[removed]/
#
# \$Revision: #11 \$
# \$DateTime: 2013/03/20 09:03:41 \$
#
# Comments/Questions? Send to [removed]@[removed].com
#
!
! love you
!!
!!!
!!!!!
!!!!!!
!!!!!!!
!!!!!!!!Snippet of the uploaded password dictionary
My conclusion? Unless Josh has taken up a side career as a black hat hacker (and he always seemed like a pleasant guy to me) his account has been compromised and there is an attack on Butterfly Labs in progress.
I immediately sent an email to Butterfly Labs warning them of the penetration but my advice to you is to stay away for a while.
Comments
comments powered by Disqus